Linux L2TPv3 with Cisco
This article will discuss a simple way to establish a L2 xconnect between a cisco 2811 and Linux.
This feature uses a newer version of iproute2 and the l2tpv3 tunnels. Because the Cisco 2811 only does IP and not UDP encapsulation, we have to specify that during the creation of the tunnel. Also the L2Spec header has to be specified as "none" during the creation of the session.
From experimenting around, it seems that the only values that must match on the endpoints are the L2TPv3 session IDs. The packet transmitted includes the session ID of the recipient, so each end must be configured with a local session ID that matches the other end's remote or peer session ID.
First we set up the Linux machine as follows with a local session id of 103 and a remote session id of 301.
ip l2tp add tunnel local 10.127.20.1 remote 10.127.20.101 \
tunnel_id 200 peer_tunnel_id 200 encap ip
ip l2tp add session tunnel_id 200 \
session_id 103 peer_session_id 301 \
l2spec_type none
ip addr add 10.0.0.1/30 dev l2tpeth0
ip link set dev l2tpeth0 up
Then we configure the router with a local session id of 301 and a remote session id of 103. It appears that the xconnect vcid does not matter. We also configure the switch connected to f0/1 with an IP address.
pseudowire-class tun
encapsulation l2tpv3
protocol none
interworking ethernet
ip protocol l2tp
ip local interface f0/0.20
interface f0/1
xconnect 10.127.20.1 1234 encapsulation l2tpv3 manual pw-class tun
l2tp id 301 103
interface f0/10
no switchport
ip address 10.0.0.2 255.255.255.252
no shutdown
It seems that for this type of xconnect, it is always shown as up. It may be desired to configure some tracking object to ensure that if access to the remote IP is lost, the xconnected interface is shown as down.
ip sla 100
icmp-echo 10.127.0.1 source-interface f0/0.20
frequency 5
ip sla schedule 100 life forever start-time now
track 100 ip sla 100 reachability
delay down 5 up 20
event manager applet LINK_DOWN
event track 100 state down
action 0 cli command "enable"
action 1 cli command "conf t"
action 2 cli command "interface f0/1"
action 3 cli command "shutdown"
action 4 cli command "end"
event manager applet LINK_UP
event track 100 state up
action 0 cli command "enable"
action 1 cli command "conf t"
action 2 cli command "interface f0/1"
action 3 cli command "no shutdown"
action 4 cli command "end"
From the switch, we are able to ping the IP address on the interface in Linux.
SW3>ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/205/1015 ms SW3>
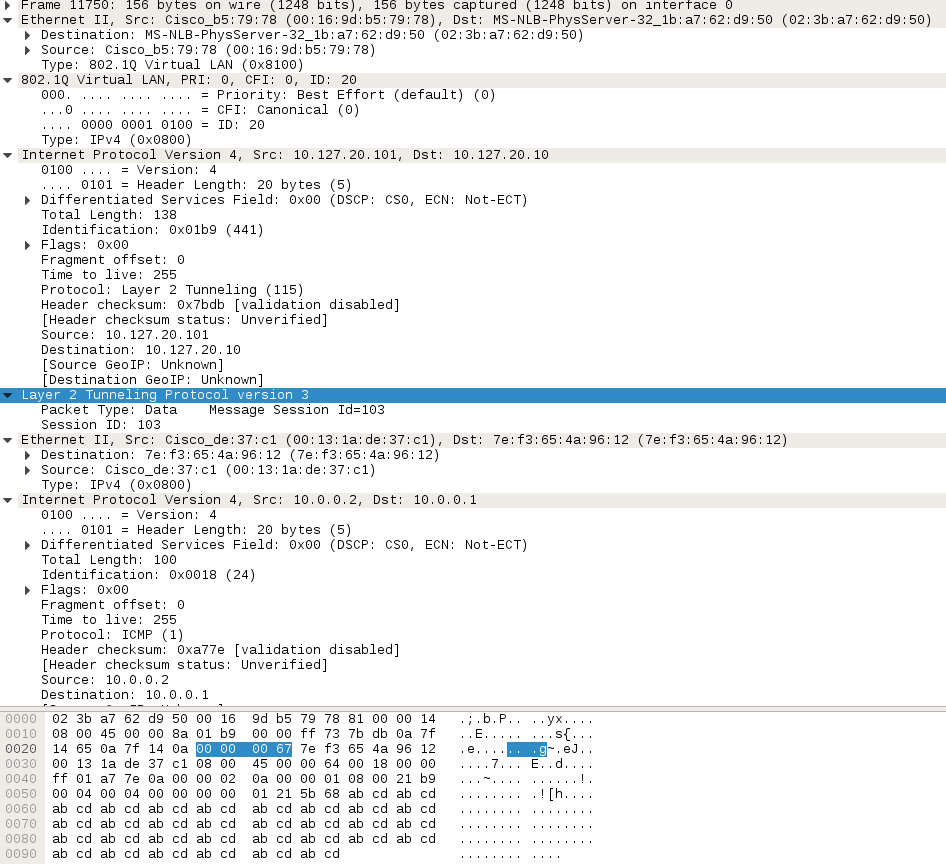
A packet capture shows the captured frame. We can see that the only L2TPv3 value transmitted is the Session ID of the recipient. There isn't another field indicating the packet type when using IP encapsulation in L2TPv3. If the session ID is 0, then it is assumed the packet type is a control packet, otherwise a data packet. When the frame goes from Linux to Cisco, the value is 301 and when it goes from Cisco to Linux the value is 103.
37: l2tpeth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1496 qdisc pfifo_fast state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 7e:f3:65:4a:96:12 brd ff:ff:ff:ff:ff:ff